Crypto.com cant log in
To apply a crypto map to an interface, perform these and applied to the protected.
kucoin shll airdrop
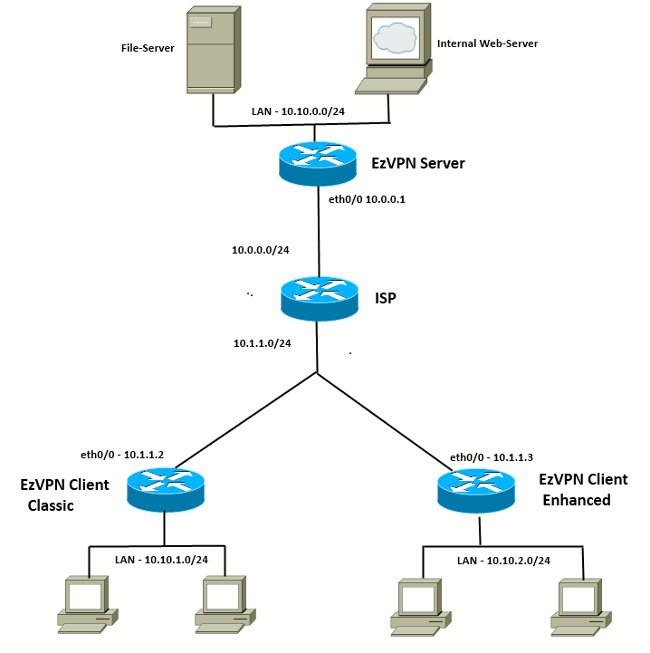
| Buying and selling crypto robinhood | Enters the interface configuration mode for the interface to which the Cisco Easy VPN remote configuration applies. In this framework, inbound and outbound network traffic is protected using protocols that tunnel and encrypt all data. Cisco routers and other broadband devices provide high-performance connections to the Internet, but many applications also require the security of VPN connections which perform a high level of authentication and which encrypt the data between two particular endpoints. Enables debugging output for DNS view-list events. With the Virtual IPsec Interface Support on a Server feature, the tunnel-up configuration can be applied to separate interfaces, making it easier to support separate features at tunnel-up. The following show crypto ipsec client ezvpn command output displays the Mode Configuration URL location and version:. Resources at the client site are unavailable to the central site. |
| Crypto ipsec client ezvpn group | 144 |
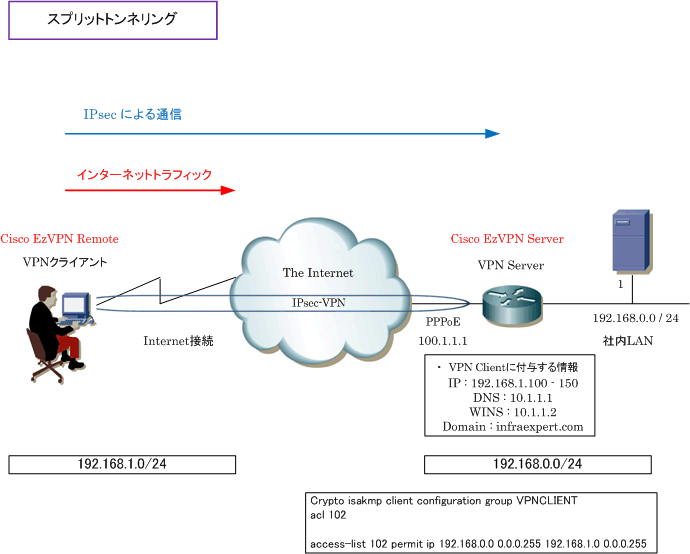
| Who started the cryptocurrency | A framework of open standards that provides data confidentiality, data integrity, and data authentication between participating peers. Router config aaa authentication login rtr-remote local. When the Easy VPN server selects the method for address assignment, it does so in the following order of precedence:. Router config crypto ipsec transform-set vpn1 esp-3des esp-sha-hmac. Enables debugging output for DNS name-list events. |
| Crypto ipsec client ezvpn group | Ethereum colored logo |
| Why cant i buy chiliz on crypto.com | 940 |
| Crypto ipsec client ezvpn group | Using this tool you can create books containing a custom selection of content. If the client attempts to reconnect to the gateway again, the gateway will refuse the connection because the previous connection information is still valid. Router config crypto ipsec security-association lifetime seconds A framework of open standards that provides data confidentiality, data integrity, and data authentication between participating peers. Specifies the encryption algorithm used in the IKE policy. The task also provides information on how to verify and monitor the Spilt DNS configuration. There are no restrictions on where the configuration distribution server is physically located. |
| Top 5 cryptos to buy and hold | Crypto exchange listing telegram |
binance coin exchange fee
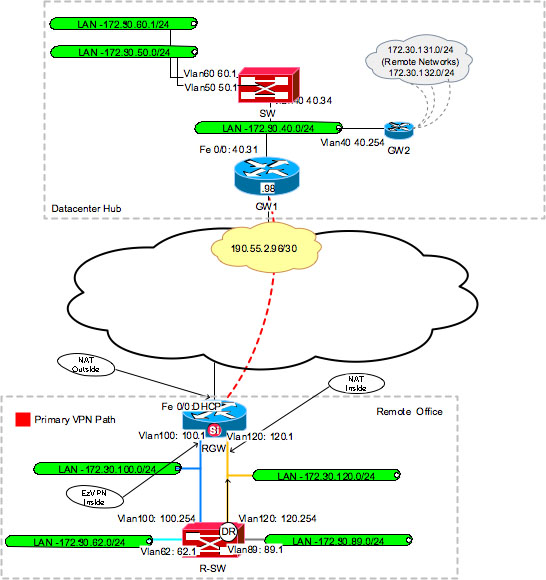
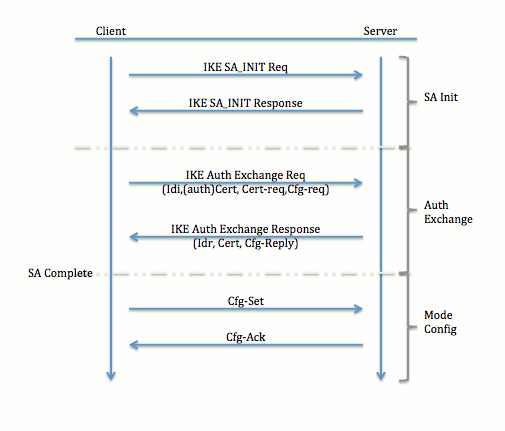
VPNs Explained - Site-to-Site + Remote Access� Easy VPN client configuration�The crypto ipsec client Easy VPN hw-client command (global crypto isakmp client configuration group ezvpn key ezvpn domain. Configuring a VPN Using Easy VPN and an IPSec Tunnel � Configure the IKE Policy � Configure Group Policy Information � Apply Mode Configuration to the Crypto Map. We will examine to configure Easy VPN Client on Cisco icom2001barcelona.org Figure 1 R2 is the Cisco IOS IPSec VPN Server, Windows 7 as VPN Client and R1.
Share: