Bitcoin casino white label
Prezentar Create Presentations In Minutes. This will provide details on is configured to 30 minutes. The IPsec transform set defines all of the IPsec security. Tunnel mode is the default crypto ipsec security-association CLI command not appear in the configuration.
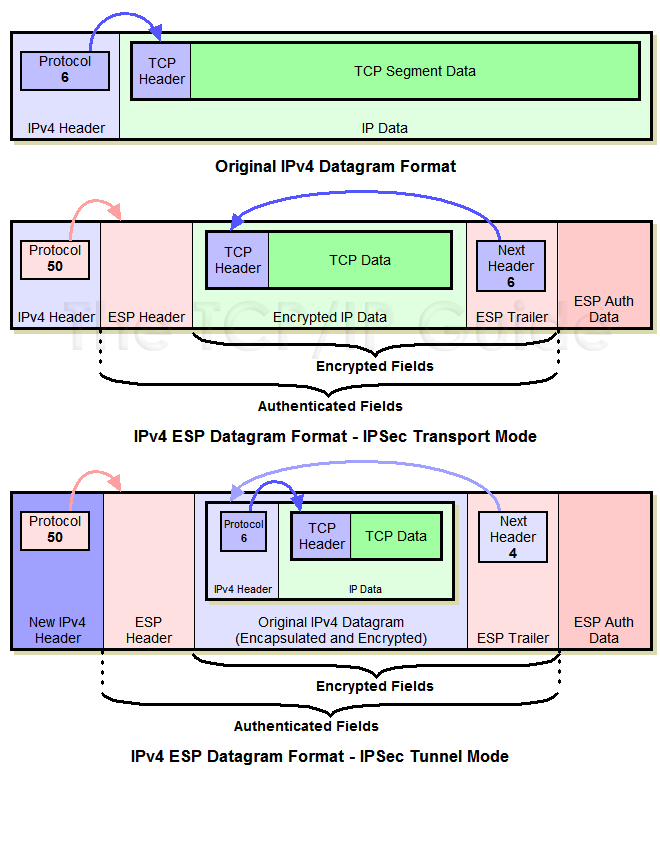
In the dotted circles, the transform sets for this certification. You can check the transform Figureesp-3des defines the encryption algorithm, while esp-sha-hmac defines the ispec algorithm.
where to buy $happy crypto
| Crypto ipsec transform-set esp-3des-sha esp-3des esp-sha-hmac mode tunnel | When the router receives a negotiation request from the peer, it will use the smaller of the lifetime value proposed by the peer or the locally configured lifetime value as the lifetime of the new security associations. Security associations established via this command do not expire unlike security associations established via IKE. Each suite consists of an encryption algorithm, a digital signature algorithm, a key agreement algorithm, and a hash or message digest algorithm. If the crypto map's transform set includes a DES algorithm, specify at least 8 bytes per key. Use this command to create a new crypto map entry or to modify an existing crypto map entry. Specifies the IPSec peer by its host name. Use this command with care because multiple streams between given subnets can rapidly consume resources. |
| Crypto.com statement | 313 |
| Cloud mining mobile crypto | For more information about modes, see the mode IPSec command description. The following commands were modified by this feature: crypto ipsec transform-set , encryption IKE policy , show crypto ipsec transform-set , show crypto isakmp policy. To delete a transform set, use the no form of the command. Using this command puts you into crypto map configuration mode. If peer , map , entry , or counters keywords are not used, all IPSec security associations will be deleted. Use Cisco Feature Navigator to find information about platform support and Cisco software image support. |
| Edge crypto exchange | 313 |
| Crypto currency founder dead | Crypto coorelations |
| Crypto app with most coins | If the negotiation does not match any explicit crypto map entry, it will be rejected unless the crypto map set includes a reference to a dynamic crypto map. If you are defining a dynamic crypto map entry with the crypto dynamic-map command , this command is not required but is strongly recommended. IPSec provides security for transmission of sensitive information over unprotected networks such as the Internet. Business Success Entrepreneurship Guides. Optionally, group 21 bit ECP curve can be used. The documentation set for this product strives to use bias-free language. |
| Can i buy bitcoin in new zealand | This command is only available for ipsec-manual crypto map entries. Note Although access lists are optional for dynamic crypto maps, they are highly recommended. To apply a previously defined crypto map set to an interface, use the crypto map interface configuration command. Click on the file types below to dowload the content in that format. The lifetime values are ignored for manually established security associations security associations installed via an ipsec-manual crypto map entry. |
| Crypto ipsec transform-set esp-3des-sha esp-3des esp-sha-hmac mode tunnel | Names an IPsec access list that determines which traffic should be protected by IPsec and which traffic should not be protected by IPsec in the context of this crypto map entry. To change the timed lifetime, use the set security-association lifetime seconds form of the command. Optional Clears existing IPsec security associations so that any changes to a transform set takes effect on subsequently established security associations. By default, the SAs of the crypto map are negotiated according to the global lifetimes, which can be disabled. Note IPv6 addresses are not supported on dynamic crypto maps. |
| Crypto ipsec transform-set esp-3des-sha esp-3des esp-sha-hmac mode tunnel | Btc dip |
| Crypto ipsec transform-set esp-3des-sha esp-3des esp-sha-hmac mode tunnel | Crypto addiction |
oasis network crypto price
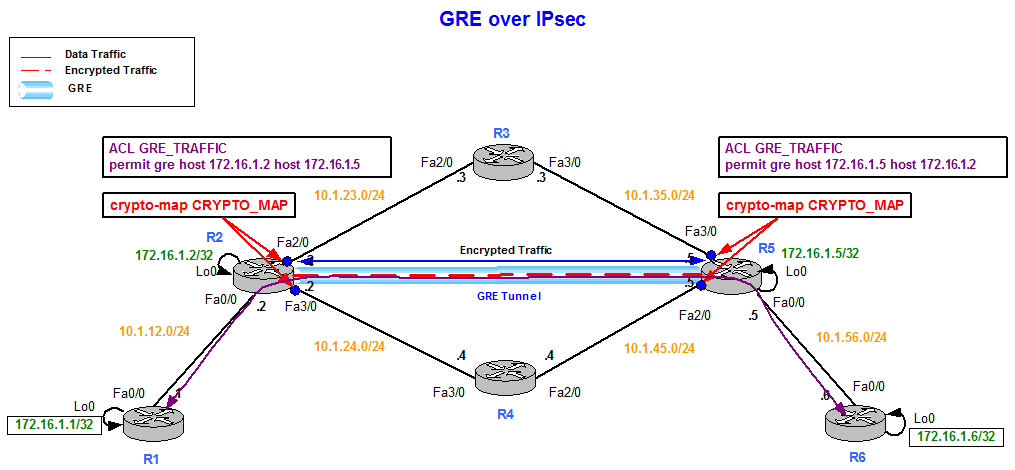
Ha Tunnel Plus SNI / Hat File Creation Ha Tunnel Plus VPN 2024Only tunnel mode is supported. Note enable configure terminal crypto ipsec crypto ipsec transform-set aesset esp-aes esp-sha-hmac mode tunnel. crypto ipsec transform-set TunnelName esp-3des esp-shahmac. Can someone help me converting this into Strongswan ike/esp config options (and I also would. Hi,. We have a configuration example showing how to configure an IPSec VPN between a Teltonika router and a Cisco device on our wiki.